Cross Site Request Forgery One Time Key Generator
- Cross Site Request Forgery One Time Key Generators
- Cross Site Request Forgery Protection
- Cross Site Request Forgery Explained
- Cross Site Request Forgery One Time Key Generator Scam
- Cross Site Request Forgery One Time Key Generator Download
How To Fix Cross-Site Request Forgery (CSRF) using Microsoft.Net ViewStateUserKey and Double Submit Cookie Overview. Cross-Site Request Forgery is an attack where a user is forced to execute an action in a web site without knowing the action ever took place. Jun 29, 2017 CSRF Mitigation for AJAX Requests. A quick recap on what Cross-Site Request Forgery is: User. Its aim is to allow sites that trust one another to break the.
No technical burden on the site owner, no difficult implementation, it's trivially simple to deploy, it's Same-Site Cookies. As old as the Web itself. Cross-Site Request Forgery, also known as CSRF or XSRF, has been around basically forever. It stems from the simple capability that a site has to issue a request to another site. No technical burden on the site owner, no difficult implementation, it's trivially simple to deploy, it's Same-Site Cookies. As old as the Web itself. Cross-Site Request Forgery, also known as CSRF or XSRF, has been around basically forever. It stems from the simple capability that a site has to issue a request to another site. Jul 29, 2014 Cross-site request forgery, also known as a one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf) or XSRF, is a type of malicious exploit of a website whereby.
In some cases, like when your buyers are using a mobile device, you want to redirect buyers to the Amazon authentication page within the same window, rather than presenting the buyer with a pop-up window.
This section covers the following information:
- Procedure - The changes you need to make to your website to enable a redirect authentication.
- Cross-site request forgery - How to prevent attackers from using a buyer's web browser to perform unwanted actions after the buyer is authenticated.
- When a buyer denies consent - How to handle cases during authentication when the buyer declines to grant you access to their Amazon Pay profile information.
Changes you need to make to your website to enable redirect authentication
- Whitelist the pages your buyers will login from and be returned to by updating allowed Javascript origins and allowed return URLs. Note: 'Allowed Javascript Origins' and 'Allowed Return URLs' can be a link. For details, see Adding allowed javaScript origins or allowed return URLs.
- In the button widget, set the popup parameter to false.
- On the webpage that you want to redirect users back to, add JavaScript code in your <header> section to retrieve the access token that is required by the widgets.
The sample code below shows JavaScript code for retrieving the access token. - Delete the widget cookie. When you use the Login with Amazon SDK for JavaScript, you can call the amazon.Login.logout method to delete any cached tokens. If you are using redirect authentication, also delete the cookie used by the AddressBook and Wallet widgets. Doing so ensures that subsequent calls to amazon.Login.authorize present the login screen by default.
The following code sample uses the amazon.Login.logout method from the Login with Amazon SDK for JavaScript to delete cached tokens.
Cross-site request forgery
Cross Site Request Forgery One Time Key Generators
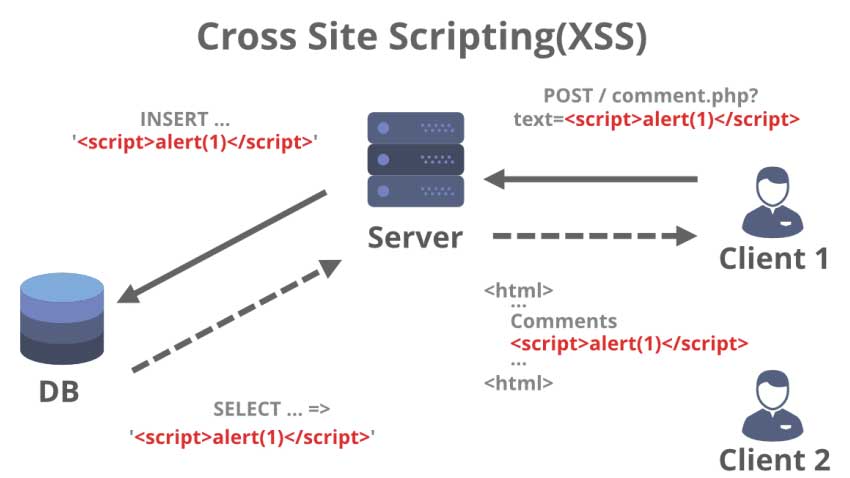
Cross-site request forgery happens when an attacker tricks a user into clicking a malicious link, where the link goes to a site where the user is authenticated. Any commands embedded in the malicious link might be executed automatically because the user is already authenticated on the site, so the user does not see a login screen or any other evidence of malicious activity. In the case of Login with Amazon, cross-site request forgery could be used to mimic a client or an authentication server.
Football Manager 2017 Product Key Generator (Keygen) Serial has built in latest security features such as proxy and VPN support, Anti ban, anti detection system. Our tools are 100% safe and clean, we do not add any hidden ads, offers or surveys to them. Football Manager 2017 License Activation Key generator! Football Manager 2017 Keygen is here and it is FREE and 100% working and legit. Before our system send cd key. Apr 07, 2017 Football Manager 2017 CD Keygen (PS, Xbox, PC) No Survey Free Download. Our game serial key generator and license key creator works for xbox one/360, pc, ps Games Hack Tools.  Football Manager 2017 Product Key Generator (Keygen) Serial’ has latest anti detection system built in, such as proxy and VPN support. You don’t need to disconnect.
Football Manager 2017 Product Key Generator (Keygen) Serial’ has latest anti detection system built in, such as proxy and VPN support. You don’t need to disconnect.
When a client registers for Login with Amazon, they are assigned a client identifier (client_id) and a client secret (client_secret). The client verifies their identity by using the client_id and client_secret parameters in access token requests (these values would have to be forged by an attacker).
Login with Amazon also uses the State parameter to prevent cross-site request forgery. The client sets the value of the State parameter when it initiates an authorization request. Unlike the client_id and client_secret values, the State value can and should be different for each authorization request. The authorization server returns the same value when communicating with the client to deliver authorization codes and access tokens. If the State parameter doesn't match the value from the initial call, the communication should be ignored. For more information about the state parameter and its use, see Cross-site request forgery in the Login with Amazon documentation.

Calculating the State parameter
Clients can calculate the State value in any way they choose, but you should ensure that the value is secure from forgery. Login with Amazon recommends using Hash-based Message Authentication Code (HMAC) to calculate State values. HMAC methodology is detailed in RFC2104. For more information, see RFC2104.
Cross Site Request Forgery Protection
To calculate a State value using this method, you must have a csrf_secret known only to the client and an authenticator message. The State value is calculated as HMAC(csrf_secret, authenticator). The authenticator value is then stored by the client.
When the state is returned by an authorization response, you can verify the state by retrieving the authenticator value and running the HMAC(csrf_secret, authenticator) calculation again. If the values do not match, you should ignore the authorization response.
When a buyer denies consent
The first time a buyer signs in and is authenticated on your website, they must give their consent to share their Amazon Pay profile information with you. If, during a redirect authentication, a buyer clicks the Cancel button on the consent screen and denies you consent, Amazon Pay forwards the buyer to the redirect URL, but instead of passing back an AccessToken, an error description is returned. Diablo 3 cd key generator.
Cross Site Request Forgery Explained
Note that an AccessToken is returned in the URL Fragment, where an error description is returned via a query string. Before rendering the redirect URL, you need to check for a query string with an error description and, if found, redirect the buyer to the page where the login process was initiated.
Cross Site Request Forgery One Time Key Generator Scam
The following example shows a URL fragment where the buyer gave their consent to share their Amazon Pay profile information with you.
Cross Site Request Forgery One Time Key Generator Download
The following example shows an error description returned in the query string when a buyer declines to share their profile information with you.