Which Algorithm Is Used To Generate A Key
Key generators are constructed using one of the getInstance class methods of this class. KeyGenerator objects are reusable, i.e., after a key has been generated, the same KeyGenerator object can be re-used to generate further keys. There are two ways to generate a key: in an algorithm-independent manner, and in an algorithm-specific manner. When they renew, you have to generate a new key. You record the plaintext name in a file and the file modify time is also part of the hashed string used to create the license key. – S.Lott Apr 15 '10 at 2:26. The algorithm would need to also have a way of expiring. Oct 18, 2016 The encryption keys generated in modern cryptographic algorithms are generated depending upon the algorithm used. Primarily there are two types of encryption schemes: Symmetric and Asymmetric(Public Key encryption). Generating Keys for Encryption and Decryption.; 3 minutes to read +7; In this article. Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. Key generation is the process of generating keys for cryptography. The key is used to encrypt and decrypt data whatever the data is being encrypted or decrypted. Modern cryptographic systems include symmetric-key algorithms (such as DES and AES) and public-key algorithms (such as RSA). Ways to generate symmetric and asymmetric keys. Ask Question. To generate such a key, use OpenSSL as: openssl rand 16 myaes.key AES-256 expects a key of 256 bit, 32 byte. Software implementing poor algorithms or good algorithms but with a buggy implementation can equally annihilate your security.
In this post I will demonstrate how to regenerate a public key from the corresponding private key that you still have.Generate public key and store into a fileIt is a simple one liner command to generate a public key from a private key, so lets say our private key is named ‘user@myserver.key’ and we want to generate the public key and name it ‘authorizedkeys’. Lets say you have a private/public key pair that you use to login to your server via SSH and you lose the public key, either it was deleted or corrupt and you don’t want to have to regenerate a new pair what options do you have? Generate ssh key openssl python.
Api key and secrete generation in php. If the random number is present in the previous ranges, the number must be discarded and then recreated. This number will then be filtered for the ranges of 58 to 64, and 91 to 96. Adding the option for the characters to repeat, creates over 450 quadrillion combinations.To keep the code short, I generate a random number using rand(48, 122).
- Which Algorithm Is Used To Generate A Key In Word
- Which Algorithm Is Used To Generate A Key Code
- Which Algorithm Is Used To Generate A Key Free
Cryptography
Derrick Rountree, in Security for Microsoft Windows System Administrators, 2011
Asymmetric Encryption
Asymmetric encryption is also referred to as public key encryption. In asymmetric encryption, both the encrypting and decrypting systems have a set of keys. One is called the public key, and another is called the private key. If the message is encrypted with one key in the pair, the message can be decrypted only with the other key in the pair.
Asymmetric key algorithms are not quite as fast as symmetric key algorithms. This is partially due to the fact that asymmetric key algorithms are generally more complex, using a more sophisticated set of functions.
Asymmetric Key Algorithms
Which Algorithm Is Used To Generate A Key In Word
Asymmetric key algorithms aren't as widely used as their symmetric counterparts. So we'll just go over two of the big ones: Diffie-Hellman and RSA.
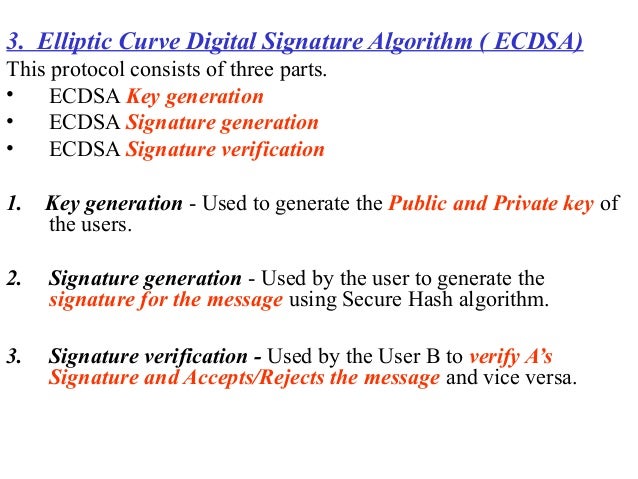
Which Algorithm Is Used To Generate A Key Code
Diffie-Hellman: The Diffie-Hellman algorithm was one of the earliest known asymmetric key implementations. The Diffie-Hellman algorithm is mostly used for key exchange. Although symmetric key algorithms are fast and secure, key exchange is always a problem. You have to figure out a way to get the private key to all systems. The Diffie-Hellman algorithm helps with this. The Diffie-Hellman algorithm will be used to establish a secure communication channel. This channel is used by the systems to exchange a private key. This private key is then used to do symmetric encryption between the two systems.
RSA: It is the Rivest Shamir Adelman algorithm. RSA was developed in 1978. RSA was the first widely used asymmetric algorithms used for signing and encryption. It supports key lengths of 768 and 1,024 bits. The RSA algorithm uses a three-part process. The first part is key generation. The keys used in the RSA algorithm are generated using mathematical operations based on prime numbers. The second part of the process is encryption. This encryption is done using one of the keys in the key pair. The third part of the process is decryption. The decryption is done using the other key in the key pair.